System Overview
The “ASP.NET Core 9 Authentication and Authorization System” is a Web API project designed to provide secure and efficient access to a bookshop’s resources. This system emphasizes user registration, role-based and permission-based access control, and secure authentication using JWT tokens. It introduces roles such as Admin, Manager, Salesman, and Customer and supports granular permissions for users within the same role. This tutorial series, published on The Coding Blueprint, begins with Part 1, focusing on foundational components like registration and seed data. Comprehensive User Story for Tutorial Series: Bookshop Authentication and Authorization System
User Stories
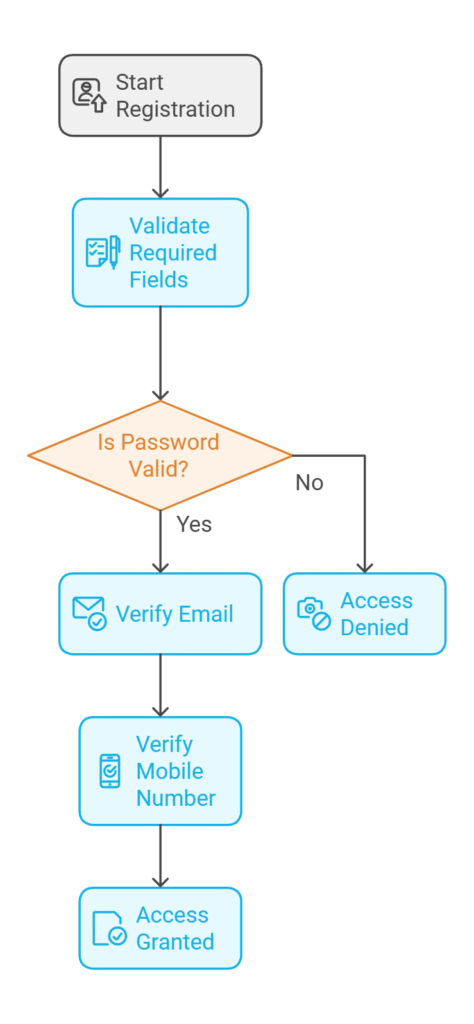
1. Registration Module
- As a customer, I want to register by providing my full name, address, date of birth, mobile number, email, and a secure alphanumeric password, so that I can create an account in the system.
- As a customer, I want to verify my mobile number and email after registration, so that my account is authenticated and secure.
- As a customer, I want my account to be temporarily locked for 15 minutes after three consecutive incorrect password attempts, so that unauthorized access is prevented.
- As a system, I need to enforce validations for all required fields during registration to ensure data quality and security.
2. Role and Permission Management
- As an admin, I want to manage roles such as Admin, Manager, Salesman, and Customer, so that I can organize user access based on their responsibilities.
- As an admin, I want to create users with specific roles (e.g., Manager, Salesman) and assign custom permissions to each user within a role, so that I can control access to certain features or data on a per-user basis.
- As an admin, I want to assign granular permissions to users with the same role (e.g., one Manager can manage inventory, another can approve orders), so that I can reflect diverse responsibilities within a role.
- As an admin, I want to modify or revoke permissions for any user at any time, so that I can adapt to changes in responsibilities or address security concerns.
- As a Manager, I want my permissions to reflect my responsibilities, which may differ from other Managers, so that I can perform my tasks effectively without overstepping boundaries.
- As a Salesman, I want to have permissions tailored to my role, such as handling customer transactions, so that I can focus on my assigned tasks.
3. Authentication
- As a user, I want to log in using my registered email and password to obtain a JWT token for secure access to protected resources.
- As a system, I want to include roles and permissions in the JWT token as claims, so that the API can enforce both role-based and permission-based authorization.
- As a customer, I want access to endpoints specific to my role, so that I can perform my tasks without interfering with other roles.
- As a Manager or Salesman, I want to see only the features or data I am permitted to access, so that my experience is tailored to my responsibilities.
- As an admin, I want to access high-privilege endpoints, so that I can manage roles, permissions, and users effectively.
- As a system, I need to validate JWT tokens for every request to ensure only authenticated and authorized users can access resources.
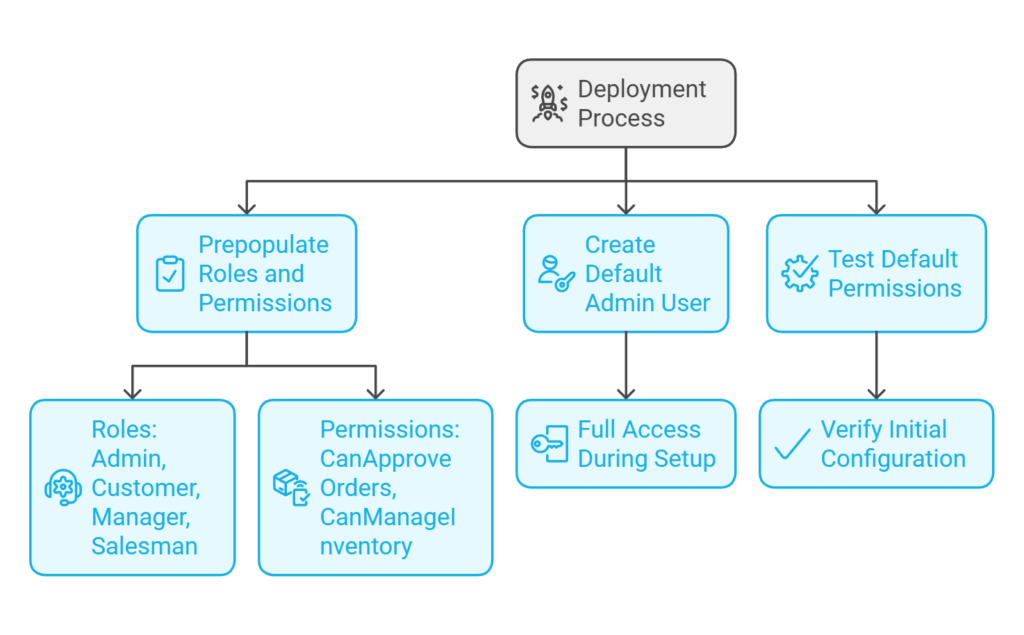
4. Seed Data
- As a developer, I want the system to prepopulate predefined roles (Admin, Customer, Manager, Salesman) and permissions (e.g., “CanApproveOrders”, “CanManageInventory”) during deployment, so that I can quickly start testing the authentication and authorization features.
- As a developer, I want the system to create a default Admin user with full access during setup, so that I can manage the system immediately after deployment.
- As a developer, I want to view and test the default permissions for each role, so that I can ensure the initial configuration meets the project requirements.
5. Permission-Based Access
- As an admin, I want to view, assign, and revoke granular permissions for individual users, so that I can ensure secure and customized access control.
- As a system, I need to enforce permissions in addition to roles when authorizing access to endpoints, so that sensitive operations are secure.
- As a Manager or Salesman, I want access to only the features and data that align with my assigned permissions, so that I do not have unnecessary access.
6. API Endpoint Security
- As a developer, I want the system to secure all API endpoints using a combination of role-based and permission-based authorization, so that the system is protected from unauthorized access.
- As a system, I need to return appropriate error responses (e.g., 403 Forbidden) when users attempt to access endpoints without sufficient permissions.
Acceptance Criteria
Registration Module
- All required fields (Full Name, Address, Date of Birth, Mobile Number, Email, Password) must be validated during registration.
- Password must be at least 8 characters long and include both letters and numbers.
- Email and mobile number verification is mandatory before granting access to the system.
- Lockout mechanism works after 3 failed login attempts for a duration of 15 minutes.
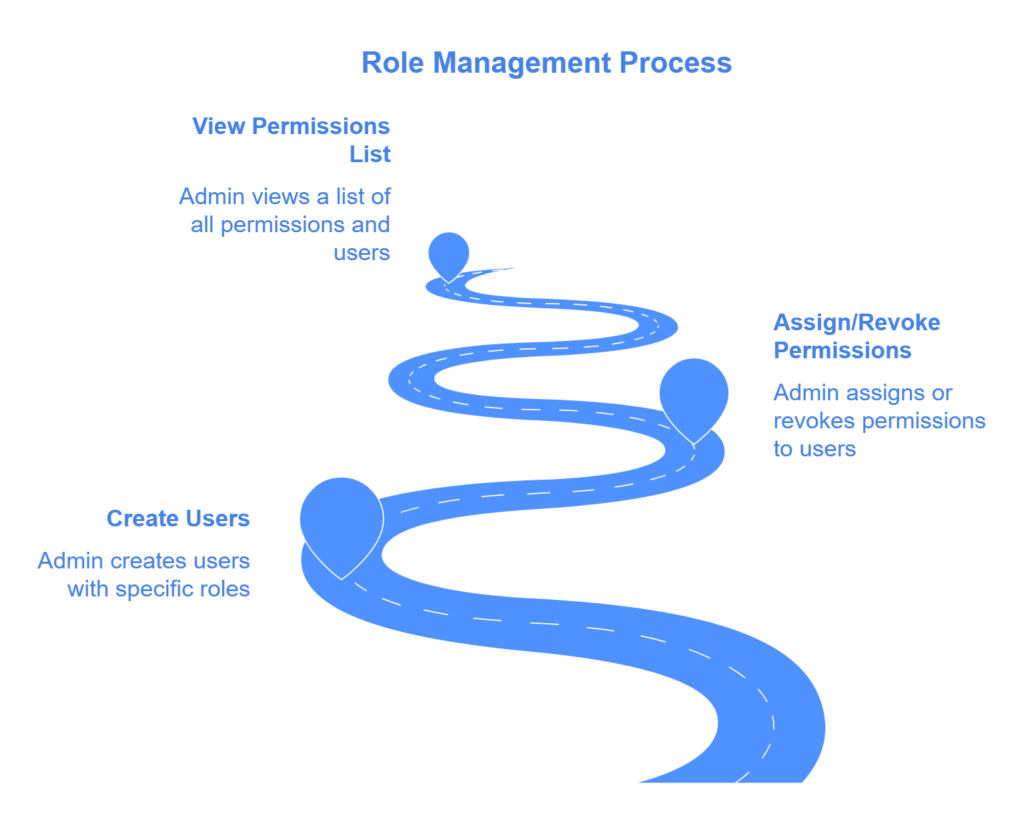
Role Management
- The system allows Admin to create users with Manager and Salesman roles.
- Admin can assign or revoke granular permissions to users within any role.
- Admin can view a list of all permissions and their assigned users.
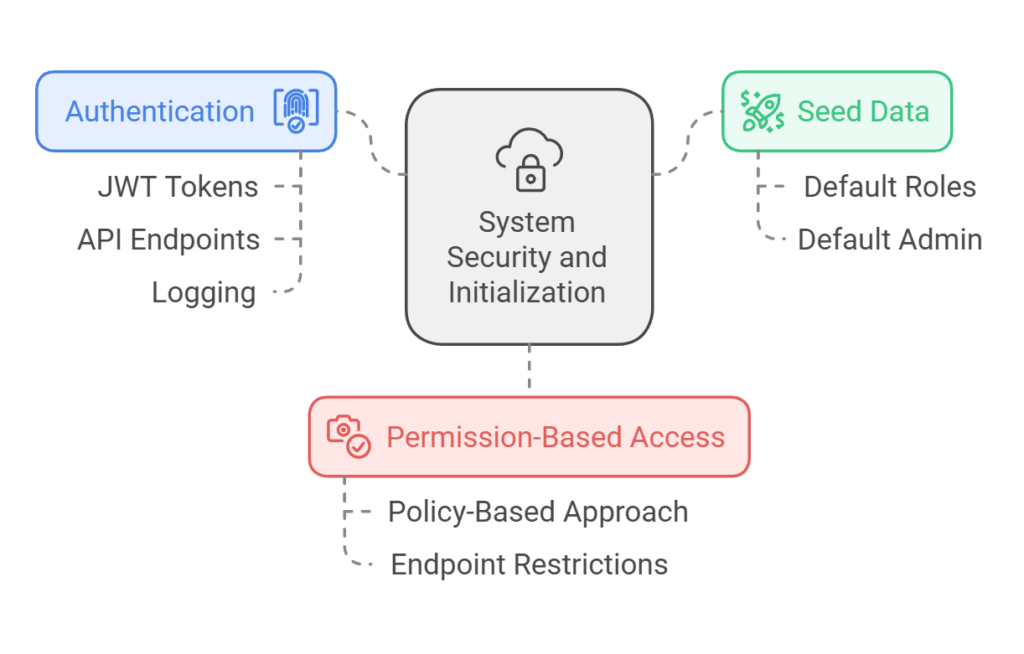
Authentication
- JWT tokens include roles and permissions as claims.
- API endpoints enforce both role-based and permission-based authorization.
- Unauthorized access attempts are logged and return appropriate error messages.
Seed Data
- The system initializes with default roles (Admin, Customer, Manager, Salesman) and permissions (e.g., “CanApproveOrders”, “CanManageInventory”).
- The system creates a default Admin user with full access.
Permission-Based Access
- Permissions are enforced for all API endpoints using a policy-based approach.
- Users cannot access endpoints for which they lack the required permissions.
Purpose of the Tutorial Series
This tutorial series, titled “ASP.NET Core 9 Authentication and Authorization System”, hosted on The Coding Blueprint, is a step-by-step guide to building a secure and flexible authentication and authorization system for a bookshop Web API.
- Part 1: Focuses on writing a comprehensive user story to define the system’s requirements, features, and use cases, forming the blueprint for implementation.
- Part 2: Covers setting up the Identity database and establishing the basic project structure to prepare for feature implementation.
- Part 3: Will dive into writing the code for the system, with detailed explanations and examples. This section will be updated as the code progresses.
The series is designed for developers of all experience levels, blending theoretical understanding with practical, real-world coding to create a production-ready application.
Some Important Links:
Link to Official ASP.NET Documentation:
- “Learn more about setting up ASP.NET Core Identity in the official documentation.”
Link to JWT Token Documentation:
- “Understand the benefits of JWT tokens for secure authentication in this comprehensive guide.”
Link to Role-Based Authorization Best Practices:
“For detailed insights into role-based authorization, check out this guide by Microsoft.”
Discover how to design and implement a robust ASP.NET Core 9 Authentication and Authorization System for a bookshop Web API. In this tutorial series, you’ll learn about user registration, role-based and permission-based access control, JWT authentication, and setting up Identity Server to create a secure and scalable application.
That was a very informative post! I’m looking forward to the next part with great anticipation.
Thanks.